Get This Report about Disaster Recovery
Its name misses out on the most damaging part of this kind of ransomware its speed. Locky has the distinction of spreading to various other data throughout the network quicker than various other ransomware strains.
The Ultimate Guide To Disaster Recovery
The significance of this aspect of the attack is that it certifies as a breach if your firm functions with personal information; companies should call anybody who may know on your network to remain in compliance with local, state, and federal standards. attacks unpatched Wild, Fly application servers in the internet-facing portion of their network.
strikes the data source web server processes to acquire accessibility as opposed to going right after the documents. Its designers sell the ransomware software to criminals for a portion of the ransom accumulated, i. e., Ransomware-as-a-Service. is a variant of ransomware representing the trend in what is called "leakware." After information is encrypted, negative stars threaten to leakage ransomed exclusive information on the dark web unless the ransom is paid.
7 Easy Facts About Disaster Recovery Described
: A modern technology in which information is equated into an unreadable type or code, and also only customers with accessibility to a secret key or password can review it. Encryption at rest and in-flight ensures the backup information, even if exfiltrated, is provided ineffective to criminals without the decryption secrets or password.
Information safety entails several layers of defense that are not restricted to the app itself: the host degree, the os degree, the customer degree, the manager level, and even the physical level of the device all have vulnerabilities that a great security system need to attend to. For this reason, application hardening may be called system setting or OS hardening.
Some Of Disaster Recovery
When calamity strikes there is commonly some downtime that includes it as employees function to recuperate data as well as get systems back up and running - disaster recovery. Downtime commonly features shed revenues due to the fact that workers can't concentrate on their day-to-day income producing tasks. Maintaining clients happy as well as coming back for more is the leading top priority of every company and also in this hectic world we stay in, customers expect excellence.
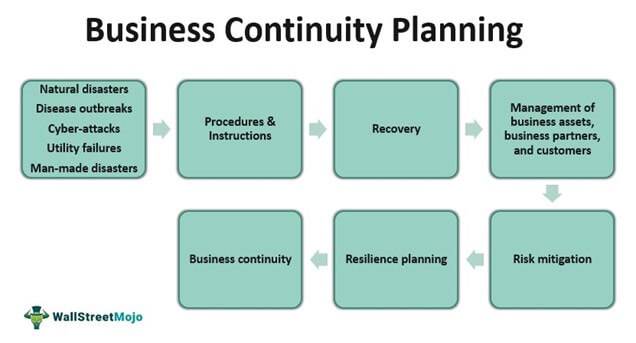
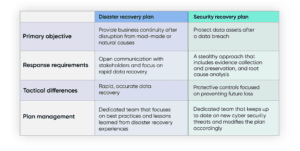
Catastrophe healing planning is an essential process for every business to go through. A disaster recuperation strategy needs determining dangers, establishing objectives of catastrophe recuperation, investigating the his response finest methods to achieve those objectives, and testing the plan.
5 Easy Facts About Disaster Recovery Described
Organizations must have an aggressive strategy to deal with supply chain disturbance triggered by cybersecurity occasions. Supply chains typically are a web of inner and also external organization procedure interdependencies with vital providers in extent. Service connection planning as well as calamity recovery methods should think about the effect of cybersecurity risks as well as threats throughout the supply chain.
A cyberattack brings in much more limelights, subjecting your organization as well as its stakeholders to greater dangers of reputational damage. It is often a pressure stove when senior management, legal, and journalism all desire answers that you may or may not have the ability to give (as well as some solutions that you should not provide).
How Disaster Recovery can Save You Time, Stress, and Money.
Below are a couple of things to think about throughout business connection preparation and catastrophe healing approach development process: Mark an Internal Communication Lead or provide that role as well as obligation to existing leadership, such as an Event Feedback Supervisor. Make certain the entire company recognizes that this person is and also accepts them in a dilemma circumstance (disaster recovery).
so all alert commitments for governing conformity are covered. There is much to think about when believing about how cybersecurity impacts business connection preparation and catastrophe recovery strategies. Proactively integrating these crucial points will go a long method to reducing the damage as well as speeding healing. Finally, if you have not established a solid company connection plan, do not wait any type of longer.
All about Disaster Recovery

A calamity recuperation plan is greater than just restoring documents; it also helps to recreate the my link service's entire IT system, consisting of data, networks and applications, to ensure that there's no loss of capability for extended time periods. Calamity healing likewise moves any kind of data from the temporary environment to the main one once back up and running.
Disaster Recovery Fundamentals Explained
A business connection plan is a comprehensive technique that makes sure the processes and also systems within a business proceed even if unintended scenarios make this tough. The need for a connection plan has actually come to be a lot more vital as cybercrime proceeds to progress as well as become much more advanced, indicating businesses require to be much more proactive in safeguarding their procedures.